Discover Hidden Secrets Worth Thousands
Our advanced scanning tool empowers bug bounty hunters to find exposed secrets across a wide range of platforms and repositories. Turn leaked credentials into significant rewards, no matter where they're hidden.
Powerful Features for Bug Hunters
Our advanced scanning engine helps you find valuable secrets that others miss.
High-Value Target Scanning
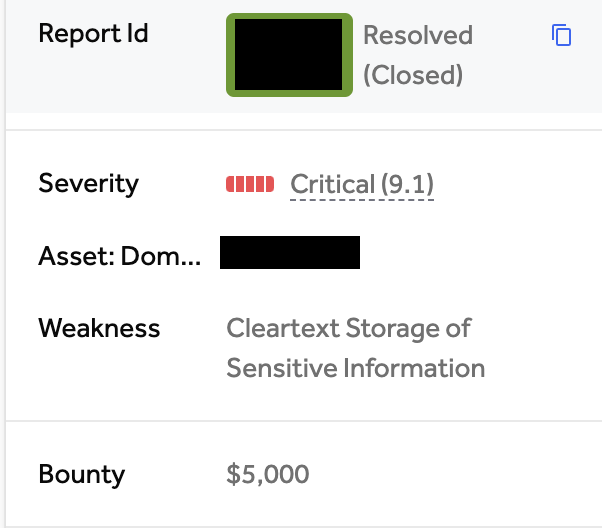
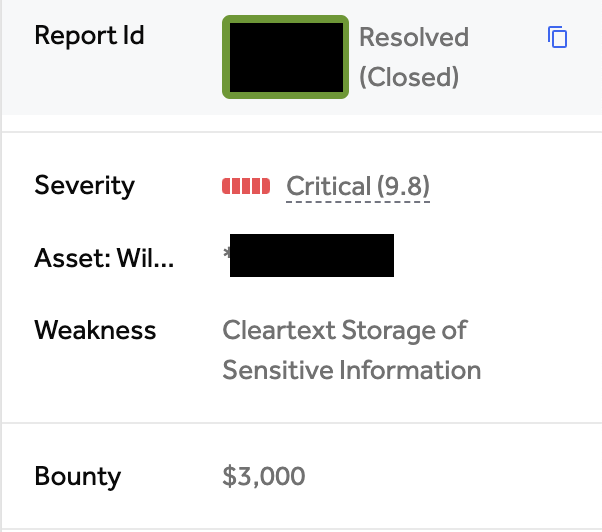
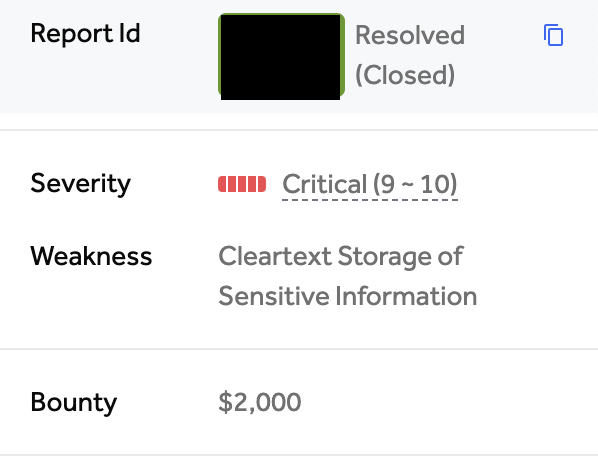
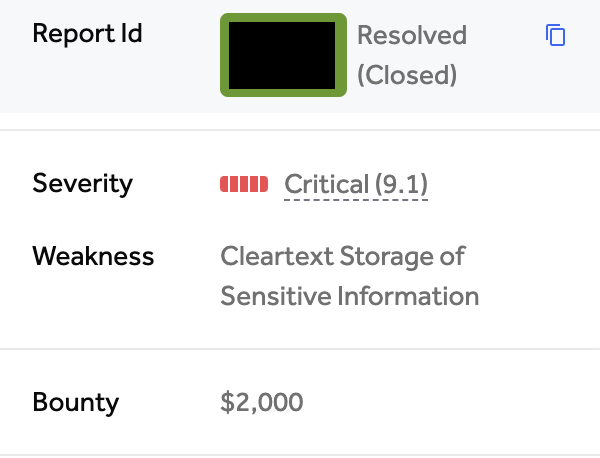
Hunt for $5,000+ bounty-worthy secrets across GitHub, GitLab, NPM, Docker, and Huggingface repositories.
- One-click organization scanning
- Multi-platform coverage
Critical Token Detection
Find and verify 300+ types of high-reward tokens including AWS, Google Cloud, and payment system credentials.
- Active token verification
- Zero false positives
Instant Bounty Alerts
Be first to claim bounties with instant notifications for newly discovered high-value secrets.
- Telegram notifications
- Discord webhook integration
Powerful Tools for Serious Hunters
Start finding valuable secrets with our flexible pricing plans designed for both beginners and professionals
Hacker Plan
For serious bug bounty hunters
- Unlimited Scans
- Secrets Verification
- Regular Updates
- Priority Support
Lifetime Access
Self-hosted scanning for pro hunters
- Private Repository Access
- Access to Private Discord Community
- Detailed Setup Instructions
- Lifetime Updates
Frequently Asked Questions
Everything you need to know about iScan.today and how it can help you find valuable secrets
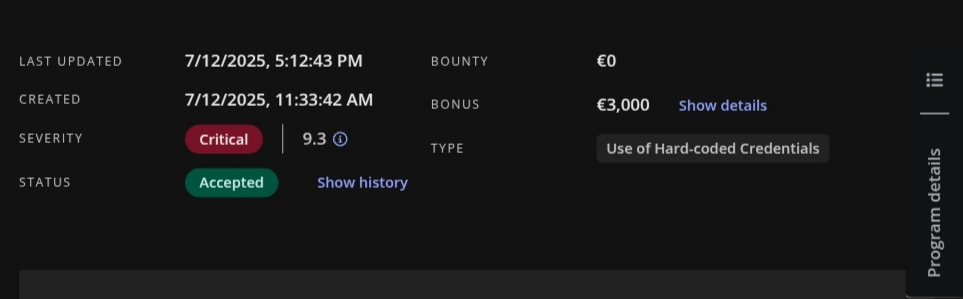
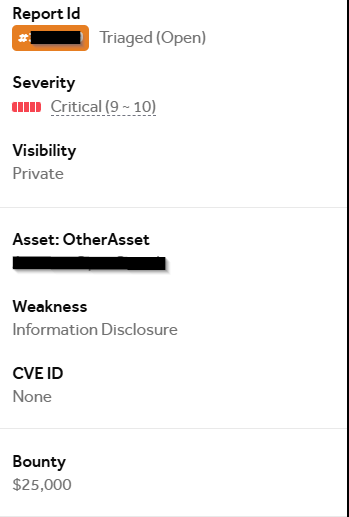
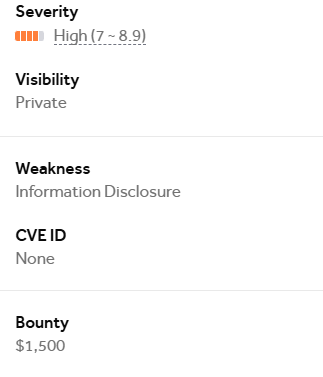
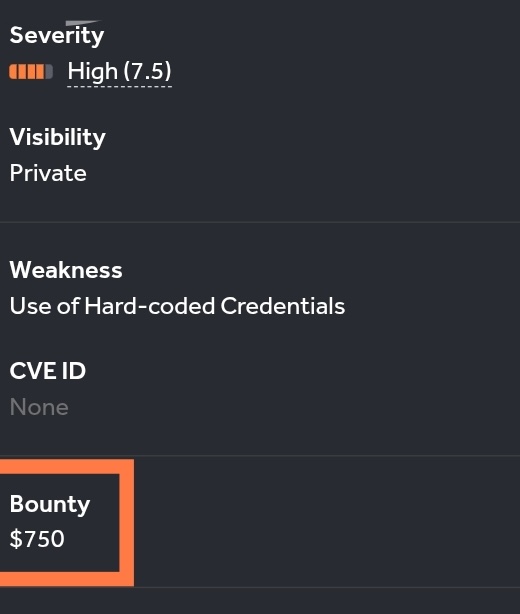
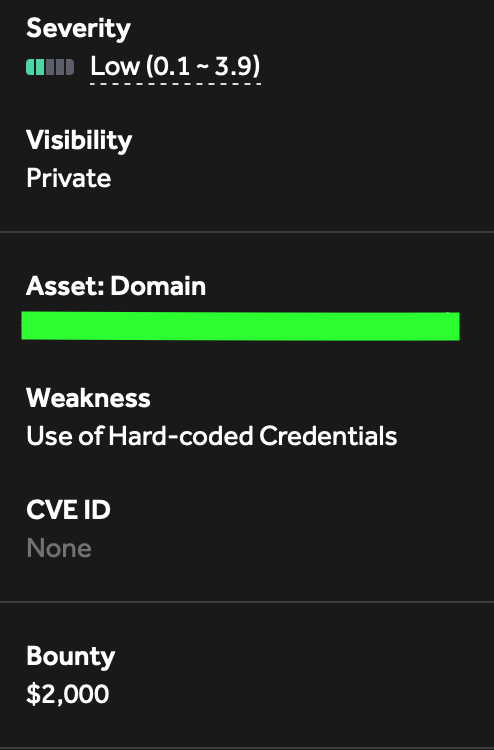
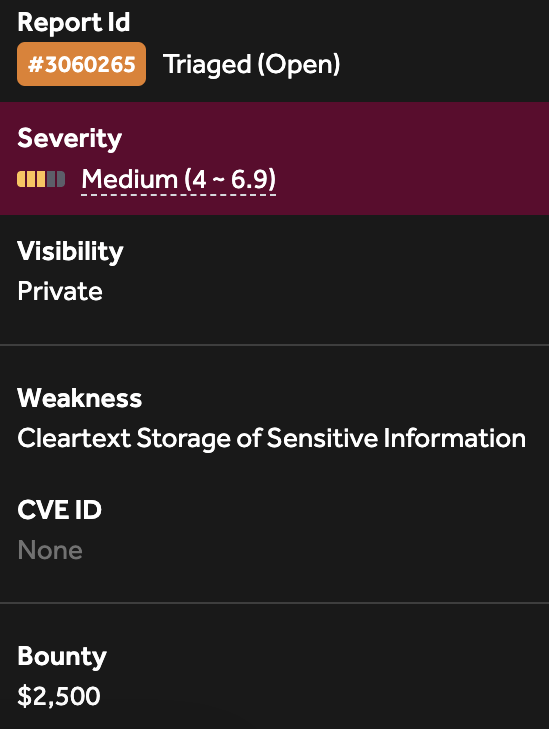
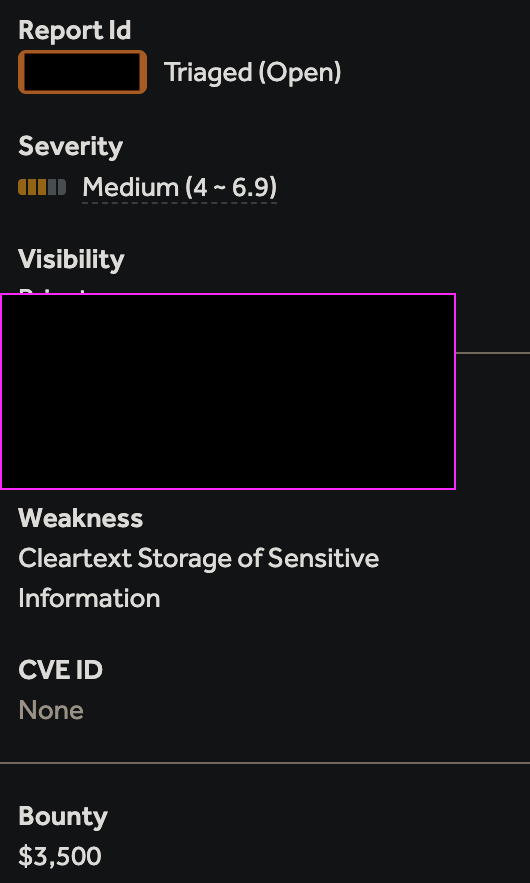
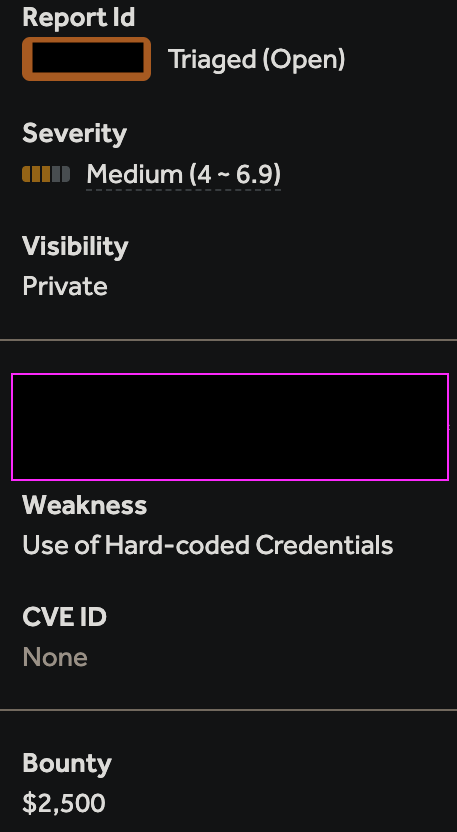
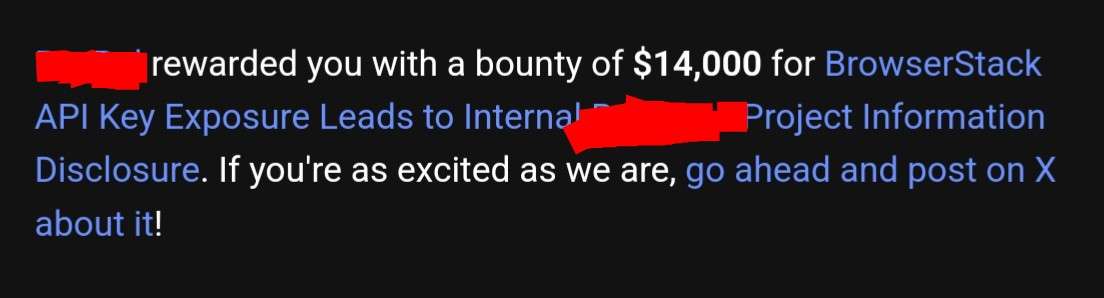
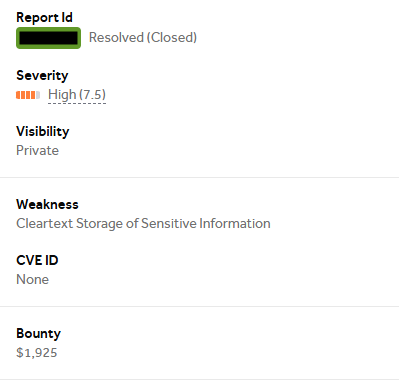
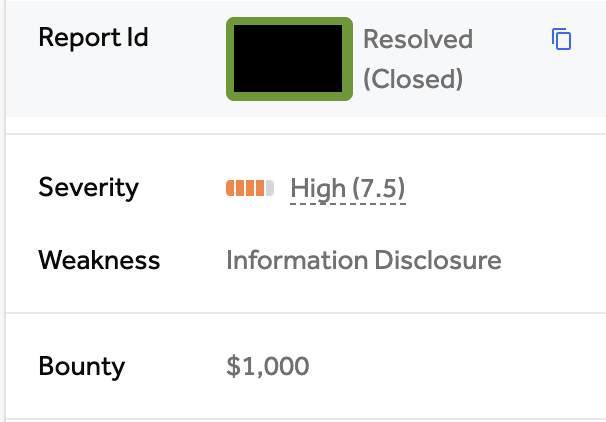
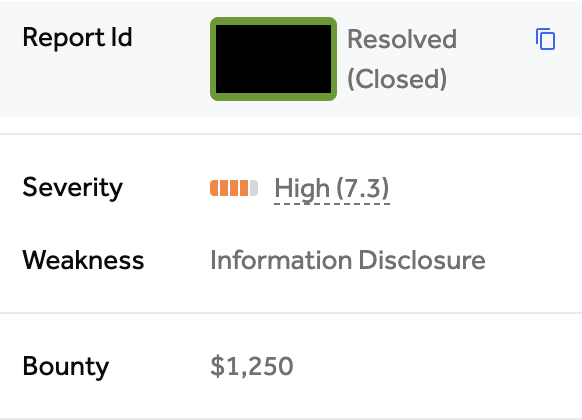
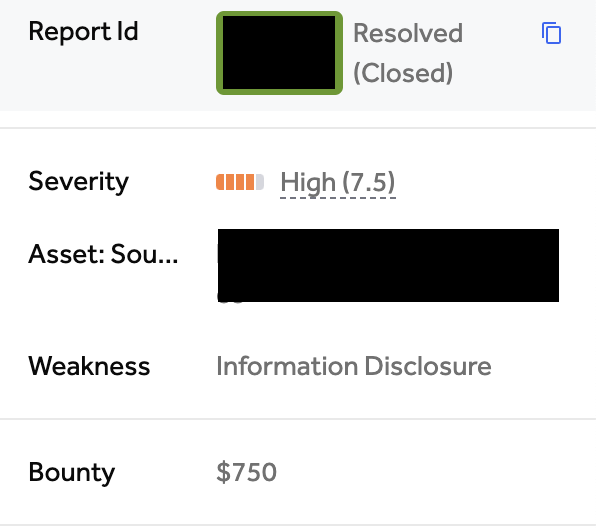
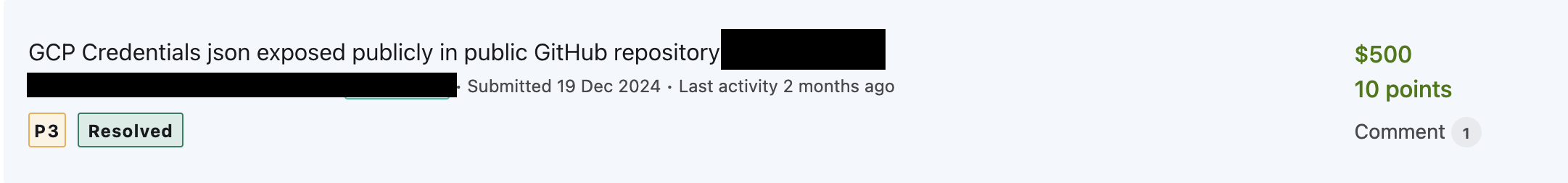
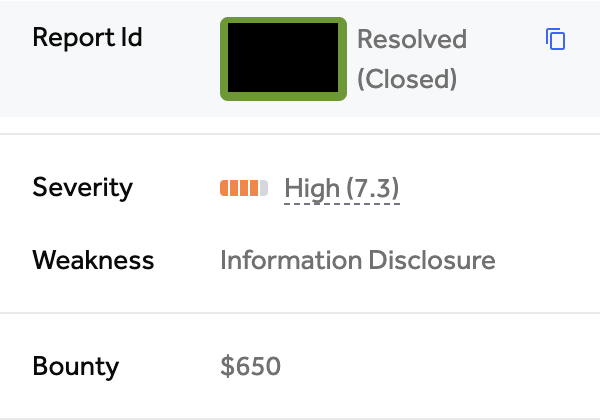
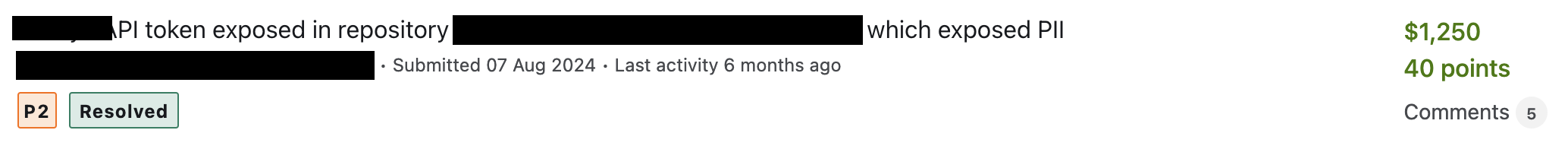
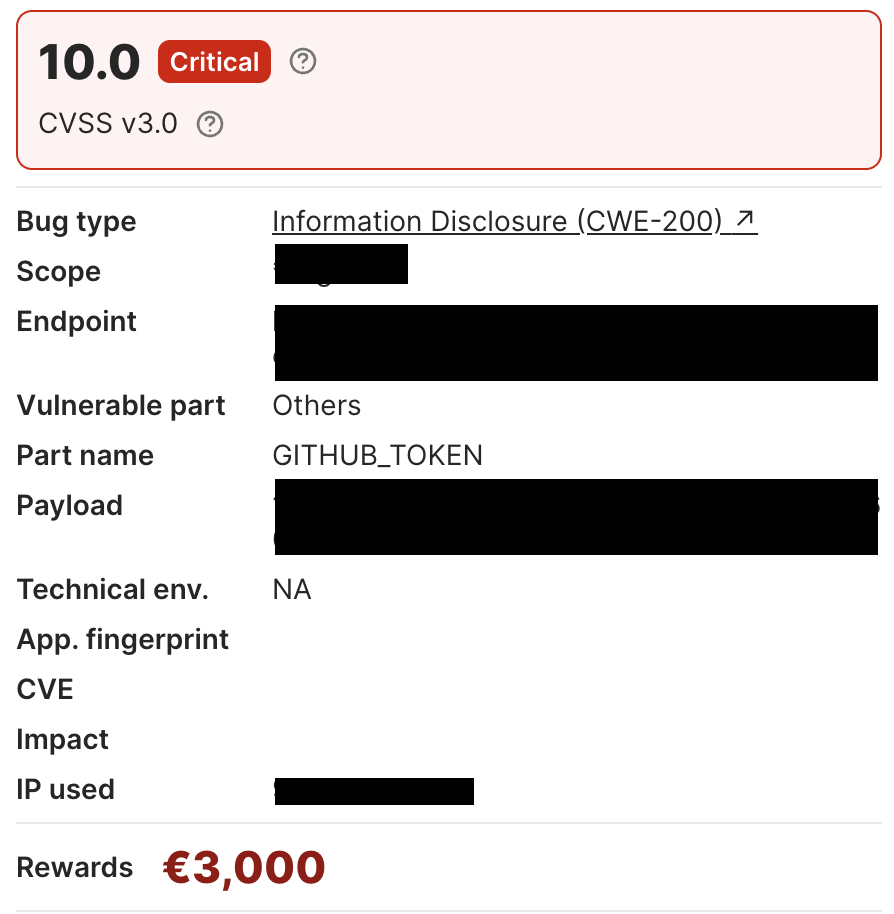
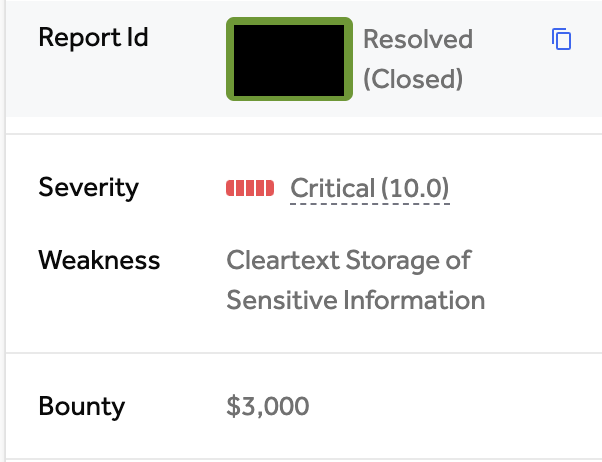
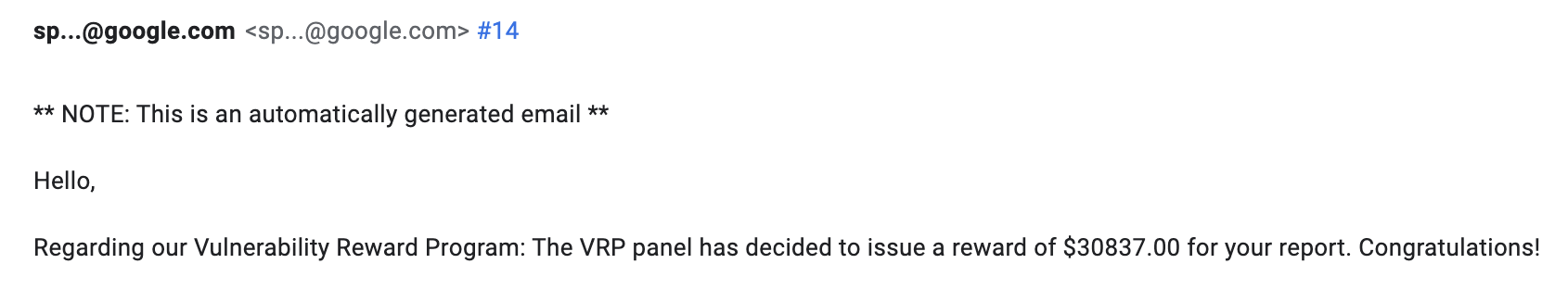
High-Value Discoveries by Our Users
Real bug bounty rewards earned using iScan's advanced scanning capabilities